Feature
End-To-End Encryption
To ensure protection in terms of file sharing, ownCloud secures all data transfers using the highly efficient end-to-end encryption.
Community Edition
Standard Edition
Enterprise Edition
ownCloud.online
(SaaS)
The importance of end-to-end encryption
End-to-end encryption is the highest level of data secrecy combined with the highest level of data protection.
It closes all possible gaps in data secrecy and data protection, setting the groundwork for a zero-trust environment in your organization. In the simplest terms, it ensures that only the sender and the intended, authorized recipient(s) are able to access the data – no one else.
End-to-end encryption is the only viable solution that can truly assure that nobody other than the sender and the recipient(s) in your organization is able to access the encrypted data, not even the system administrators.
Who it is for
End-to-end encryption is strongly recommended for your enterprise if it deals with sensitive and valuable data, for example, personal details, financial data, healthcare records, and the like.
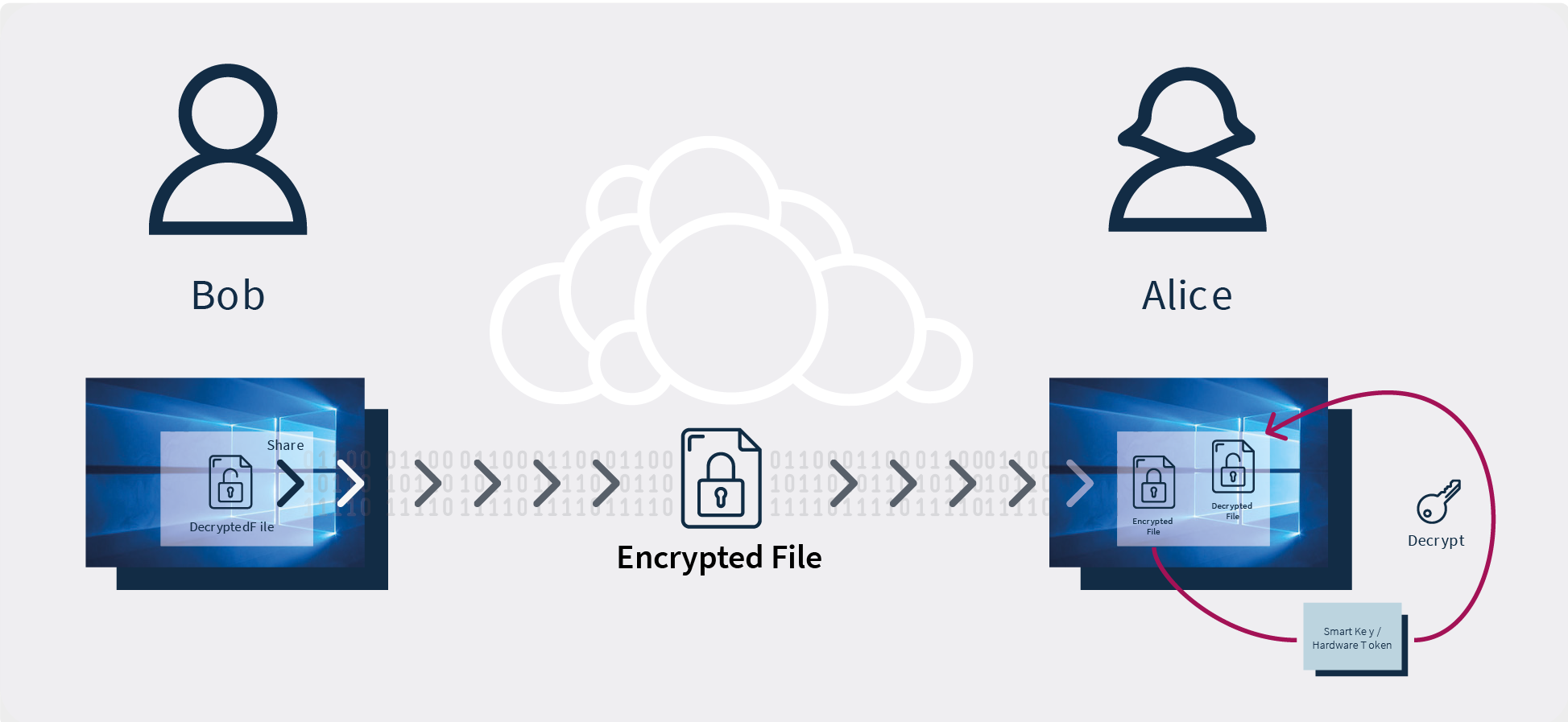
How it works:
A user uploading files can view a list of users who have access to the files. Before uploading to the server, each file is encrypted inside the browser leveraging a JavaScript plugin delivered to the user’s browser securely. The files are encrypted with public keys fetched from the server. The decryption mechanism takes place inside the browser as well with the use of the private key in the browser.
For a further level of data security, ownCloud provides an additional key service. The key service assures that the private key can be kept outside of the browser, even in the form of a smart key.
Advantages of ownCloud end-to-end encryption at a glance:
- It ensures that only the sender and the authorized recipient(s) are able to access the data.
- It promises a superior level of data security, data privacy and data secrecy.
- It allows for full user control and a transparent overview of user access.
- This centralized setup eliminates the need for installing additional software and cumbersome multiple encryption and decryption systems, making it an easy and user-friendly system of file sharing.
- The encryption and decryption processes take place directly in the browser.
- To prevent unauthorized access of the private key, it is possible to outsource the decryption of the file key to an external key service, which also supports communication with external hardware tokens.
- In this setup, in the course of file sharing, neither the sender nor the recipient is bound to a specific environment.
- It enables sending and receiving fully-encrypted emails.
Limitations:
With end-to-end encryption enabled, it is not possible to leverage collaborative editing or any server-side function including virus scanning.
Also, in this setup, the user needs to consider the secrecy or data protection requirements of files in each folder and the performance overhead on the client side. It is also important to keep in mind that the system administrator can’t recover any data for the user. If the private key is lost, the data cannot be decrypted in any other manner.

